Another weekend in the UK and Facebook users are both being SWAMPED and are SWAMPING the web with fake voucher codes AGAIN!
Despite repeated warnings by supermarkets and trading standards across the country, there seems no let up in the social sharing of these codes along with the very high chance of having identities stolen or at the very least being added to email spam lists.
The method of sharing these scams are by using ‘Social Engineering’, ie. Friends and Family share them and add legitimacy to an other wholly illegitimate fraud.
By clicking on these fake vouchers and accepting what appears to be a vaguely official looking terms and conditions, people are effectively handing over their personal details in return for absolutely nothing…
So, what are the giveaways?
-

An example FAKE voucher The vouchers contain an expiry date in US date format
- The barcode is the same for each voucher, these would need to be unique.
- The issuing store is ALWAYS Greenhithe.
- It can ONLY be redeemed with your original receipt
- All of the vouchers seem to mention ADSA Direct rather than the store they are supposedly issued under.
- The domain name is suspicious to say the least, The URL has not relation to Morrisons other than a VERY DUBIOUS domain name.
All of these would lead me to be extremely suspicious of the validity of the offer. So let us look at the domain name morrisons-f50f83o.grabinn.us
For starters I see no logical reason for any large company to be using such a cryptic URL for anything, but lets look at where this website lives. We do this by using a common command call ‘ping’.
ping morrisons-f50f83o.grabinn.us. PING morrisons-f50f83o.grabinn.us (178.32.50.152): 56 data bytes 64 bytes from 178.32.50.152: icmp_seq=0 ttl=49 time=31.111 ms 64 bytes from 178.32.50.152: icmp_seq=1 ttl=49 time=31.736 ms 64 bytes from 178.32.50.152: icmp_seq=2 ttl=49 time=32.421 ms 64 bytes from 178.32.50.152: icmp_seq=3 ttl=49 time=30.546 ms
We are returned an IP address, this is the physical address that this voucher code lives at, in the case of this voucher code it resolves to 178.32.50.152
We can then lookup the IP using domaintools.com and it gives the following results
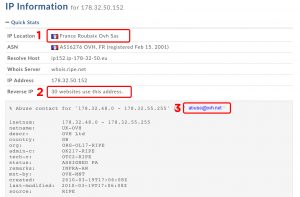 The host (or computer holding the web site is located in France. This makes the tracing of the owner much more difficult as it requires international law enforcement cooperation
The host (or computer holding the web site is located in France. This makes the tracing of the owner much more difficult as it requires international law enforcement cooperation- This shows that 30 other websites are located on the same server. I would suggest these are probably variants of the web address, possibly other store names.
- This is the ‘abuse’ contact for this IP address, in this case it is [email protected] . This is the email address people should contact to report unlawful behaviour. Worth noting.
We now have the contact details of the host in order to report unlawful behaviour.
OK, we can now lookup the domain name to find out it’s owner. In this case it is using subdomains, so we can comfortably ignore the morrisons and hieroglyphics and concentrate on the TLD or Top Level Domain grabinn.us
 GRABINN.US is the domain name used to host the voucher
GRABINN.US is the domain name used to host the voucher- NAMECHEAP is the registrar (or company holding the domain name)
- Lisa Alex is the registered owner of the domain (probably a fake name)
- This is the registered address of the domain owner (probably fake too), it doesn’t look like a valid address and the telephone and fax numbers are also fake looking.
So, by the look of everything, we have a domain name that cost 99p to register using a LOW COST registrar, hosted on a server that charges £1.60 per month on a LOW COST server by a fake name at a fake address in Pakistan (supposedly).
Now, YOU need to ask yourself the following question,
Would a multinational company employ a person to run it’s national voucher system whilst sitting behind fake credentials on low cost hardware? Or would they use their own existing IT infrastructure?
Why not spend the time you might have spent being duped by reporting these people to the ‘abuse’ email address and help STOP this kind of thing from continuing.
If you live in Suffolk or Norfolk, we now have our own Cyber & Serious Crime Department which can be contacted by dialling 101. I have spoken to several officers working in this division and they are all very professional and take cyber crime very seriously.

